What Is Zero Trust Network Access?
1 What is Zero Trust Network Access (ZTNA)?
ZTNA, or Zero Trust Network Access, is a security framework that helps you secure your network. It doesn't just trust anyone, whether they're inside or outside the network's borders. In today's constantly and rapidly evolving digital landscape, preventing cyber attacks using traditional network security measures is pretty impossible.
In this scenario, Zero Trust Network Access (ZTNA) has gained notable traction and has emerged as a revolutionary approach to security. Hence, this blog will discuss Zero Trust Network Access (ZTNA) and how it works.

The traditional security models work on perimeter-based defenses. However, the Zero Trust Network Access security framework relies on the 'never trust, always verify' concept. It authenticates every device, application, and user trying to access the network, regardless of location or connection. Here is how it can be used across multiple objects:
2 ZTNA Use Across Multiple Objects
1 Devices
ZTNA authenticates every device trying to get into the network by verifying its identity and security posture. It stops unsecured and compromised devices and eliminates the risk they pose to the network.
2 Applications
With applications, ZTNA only grants access based on predetermined policies to ensure that only the specifically authorized users get access. It decreases the possibility of cyber-attacks.
3 Network Infrastructure
Organizations enhance network traffic visibility and control, minimizing vulnerability to potential threats by implementing a Zero Trust Network Access approach to network infrastructure.
4 Cloud Services
In the era of remote jobs, ZTNA ensures secured access to cloud resources and services for remote devices and users. It helps to diminish unauthorized access to the network and sensitive data.
3 How Secure is Zero Trust Network Access and How It Works
How secure is ZTNA? As stated earlier, the Zero Trust Network Access security framework relies on the 'never trust, always verify' principle. The ZTNA security model assumes that trusting any network object without checking first is a big no-no.
Hence, before allowing access to the network, it authenticates every device, user, and application. Even if the objects are inside the network, ZTNA constantly checks and ascertains them to ensure they will not pose any threat.
Now, we will understand how Zero Trust Network Access works.
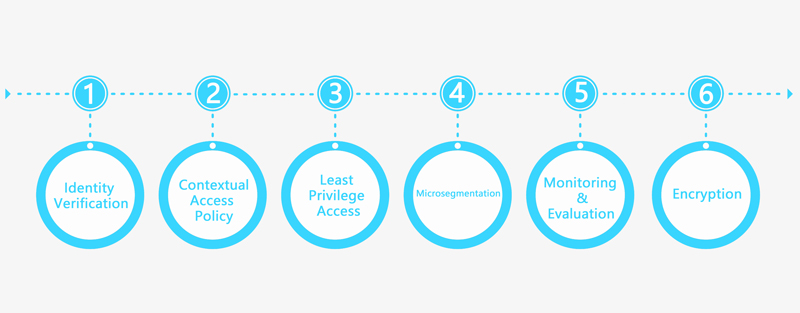
How Does ZTNA Work?
Below are the various steps involved in its implementation.
1) Identity Verification: The foremost step in the ZTNA process is identity verification to ensure that only the authorized device or user gets access. Each user, device, or application trying to hop onto the network needs to authenticate itself via robust authentication mechanisms like MFA (multi-factor authentication).
2) Contextual Access Policies: After identity verification, it is time to apply contextual access policies. It analyses elements including device security posture, device and user location, user's role, and network context to decide the level of access you need to grant.
3) Least Privilege Access: Giving too much access to any device, user, or application can cause a network and data security breach. Hence, ZTNA relies on a least privilege access code. It only allows the resources and access to the users, devices, and applications essential for completing the tasks designated to them.
4) Microsegmentation: Zero Trust Network Access security framework divides an enterprise's network infrastructure into tiny and isolated segments (micro-perimeters). It is also known as microsegmentation. This component of ZTNA gives feasibility to secure each network segment separately to avoid spreading any security threat. In case the security of any particular segment is breached, the other segments remain safe.
5) Monitoring and Evaluation: It is crucial to monitor and evaluate the network security constantly. ZTNA enables an enterprise to detect and respond to threats in real-time. It helps to monitor the network traffic and user behavior continuously so that the organization can find suspicious activities and take the required security measures to dissolve the threat.
6) Encryption: Encryption is one of the most crucial elements of data security. In ZTNA, all the data in transit between the users, devices, and applications or at rest is encrypted. Even if someone tries to peek, robust encryption algorithms help prevent data leaks and any other security breach, as the intruder cannot understand anything.
Now that you know how secure Zero Trust Network Access is and how it works, let's discuss its benefits.
4 Benefits of Using Zero Trust Network Access Technology
Zero Trust Network Access (ZTNA) has various benefits, including unauthorized access prevention, reduction of insider threat risk, and secured access for remote and BYOD users. Below, we are going to discuss the significant advantages of using ZTNA:
- Improved Network Security and Unauthorized Access Prevention
- Minimizes Risk of Insider Threats
- Protected Access for Remote and BYOD Users
Improved Network Security and Unauthorized Access Prevention
Zero Trust Network Access security framework relies on the 'never trust, always verify' principle. Hence, there are lower chances of unauthorized access as ZTNA authenticates every device, user, and application before granting any access to the network.
Minimizes Risk of Insider Threats
ZTNA applies contextual access policies and the least privilege access principle to minimize insider threat risk. The security framework analyzes each element, including device security posture, device and user location, user's role, and network context. Based on the least privilege access principle, ZTNA grants only the required access to employees per their roles and responsibilities.
Protected Access for Remote and BYOD Users
ZTNA ensures secured access to resources, services, and networks for remote and BYOD (Bring Your Own Device) users. It helps to diminish unauthorized access and ensures protected access to the network and sensitive data regardless of the location and device.
5Concerns of Zero Trust Network Access
Just like anything, Zero Trust Network Access also has some blemishes. Despite being a robust enterprise network and data security framework, ZTNA has some concerns you must know about. Below are some of the considerable risks of using Zero Trust Network Access technology.
1 Attacks On User Credentials and Admin Account Susceptibility
There is a threat of attacks on user credentials and admin accounts. Hackers can try to sneak and get credentials for user and admin accounts. However, enterprises can reduce this risk by executing a powerful authentication mechanism.
2 Potential Impact on Network Performance
Continuous verification and inspection of network traffic can harm the performance of an enterprise network. It makes the network sluggish and can directly affect productivity.
3 Effect On User Experience Due to Strict Access Controls
Strict access controls and constant verification have a direct effect on user experience. It gets arduous for users to constantly verify their identity, affecting their efficiency.
4 ZTNA Model Complexity Can Cause Errors and Misconfigurations
We all know how complex the ZTNA model is. It requires high-level expertise to implement, manage, and monitor Zero Trust Network Access. Hence, it might cause errors and misconfigurations, leading to performance issues and security breaches.
5 Costly and Requires Ongoing Administration and Maintenance
ZTNA is a potent framework for network security and monitoring, but it requires ongoing administration and maintenance that comes with a cost. Hence, it can affect the overall budget of the enterprise.
6 ZTNA vs. VPN
Instead of ZTNA, many enterprises use a VPN (Virtual Private Network) to manage network access. Hence, we have compared ZTNA with a VPN based on factors like access control, security model, user experience, and visibility and monitoring. It will help you decide which one to choose for network security and monitoring.
ZTNA | VPN | |
|---|---|---|
| Access Control | Granular control based on user/device role, posture, and other contextual factors. | Broad access control and based on network location and login. |
| Security Model | Relies on the 'never trust, always verify' model. | Depends on the castle-and-moat (perimeter-based) model. |
| User Experience | Generally frictionless as network access is based on user identity and contextual factors. | Users might have to take extra steps and face speed and performance issues due to traffic routing. |
| Visibility & Monitoring | Continuous advance monitoring and granular visibility offering deeper and real-time insights. | Less advanced monitoring and somewhat limited visibility outside network endpoints. |
After the above comparison between ZTNA and VPN, we can clearly say that ZTNA offers more granular access control. It follows the 'never trust, always verify' model, lowering the chances of unauthorized access compared to a VPN that relies on a perimeter-based model.
Concerning the user experience, ZTNA is the winner here and offers a frictionless user experience. Zero Trust Network Access also provides more advanced visibility and real-time monitoring compared to a Virtual Private Network.
7 ZTNA vs. Traditional Network Security Model
Now, we will compare ZTNA with the traditional network security model to help you understand which is better in today's constantly evolving digital landscape. The comparison will be on different aspects, including trust model, access control, network segmentation, user verification, and threat response. It will help you get a comprehensive overview of both ZTNA and the Traditional Network Security Model.
ZTNA | Traditional Network Security Model | |
|---|---|---|
| Trust Model | Zero trust - always verify the device, user, or application trying to access the network. | Trust-based - do not verify the devices, users, or applications already on the network. |
| Access Control | Based on identity, context, and device posture. | Based on username/password, with some additional multi-factor authentication. |
| Network Segmentation | Enforced through microsegmentation and software-defined perimeters (SDP) rather than VLANs and firewalls. | Enforced through VLANs and firewalls. |
| User Verification | Constant verification based on user activity and risk assessment. | Verification only at initial login. |
| Response to Threats | Quick response to detected threats, enabled by microsegmentation that limits lateral movement. | Response to threats is reactive, relying on existing security solutions that monitor traffic. |
As we can see in the above comparison, ZTNA is better than the traditional network security model in every aspect. It is apt for the current environment where enterprises have remote workers, and the number of devices accessing an organization's networks increases continuously.
8 Use Cases of Zero Trust Network Access
Enterprise network security is promptly shifting to the 'never trust, always verify' model. Hence, in this ever-evolving and rapidly changing digital landscape, Zero Trust Network Access can be used to address several network, data, and cloud security challenges. Here, we will discuss the use cases of Zero Trust Network Access technology.
Remote Work
Remote employees can securely access the enterprise resources and network from anywhere with the help of Zero Trust Network Access. It authenticates user identity, device security posture, device and user location, user's role, and network context to ensure that every network access is authorized.
Bring Your Own Device (BYOD) Policies
ZTNA helps enterprises ensure secured access to their resources, services, and networks for remote and BYOD (Bring Your Own Device) users. It facilitates safe access for employees' personal devices that they use in the organization's network.
ZTNA technology verifies that the personal devices also comply with the network security policies of the enterprise before granting any access.
Third-Party Access
ZTNA allows a secure pathway to grant access to third-party vendors and business partners. The network access security technology authenticates the identities and devices of the third-party vendors before granting controlled network access to them. With ZTNA, enterprises can lower the risk of third-party network security breaches.
Access to Cloud Applications
Organizations can use the Zero Trust Network Access framework to implement granular access controls before granting any network access to the cloud. It also helps to refuse access to any specific cloud-based application, adding an extra security layer to protect sensitive data.
Final Words
In conclusion, Zero Trust Network Access (ZTNA) is a mighty network security framework that provides improved security and control over network access, enabling enterprises to mitigate cybersecurity risks in the modern digital landscape.
Still need help? Submit a request >>

