How to Secure Remote Access IoT Devices & Best Tools
Benefits of IoT Remote Access for Enterprises
In the past decade, the IoT industry has been at the forefront of regular discussion in the mass media, revolutionising various important sectors. IoT has been invaluable due to two defining features that categorise its concept. These being:
Automation: The direct communication between separate devices without the need for human interference.
Connectivity: Enhanced connections within a global network enable easy access to vast amounts of information.
IoT remote access offers many enterprises significant and undeniable benefits such as helping companies with key issues including improved productivity, efficient operation management, cost-effective operation, and improved work safety. And configuring secure remote access IoT is fundamental to effectively harness it.
- 1 : Security - Challenge Facing Remote Access of IoT Devises
- 2 : Best Practices for Secure Remote Management of IoT Devices
- 3 : Can Someone Remote Manage IoT behind Firewall?
- 4 : AirDroid Business MDM - Secure Configure the Android Device Remotely

- 5 : Security and Privacy Features of AirDroid Business MDM
- 6 : How Remote Access Impacts IoT Devices?
- 7 : Samples of Remote IoT Management for Any Industry
- 8 : FAQs about Remote Access to IoT Devices
- 9 : Learn More: What is the Best Way to Secure IoT Devices
hide
1 Security - Challenge Facing Remote Access of IoT Devises
The potential for the IoT is enormous, as it provides the possibility for the fluid autonomous interaction of devices and systems across industries. However, as mentioned previously, several challenges, risks and vulnerabilities face IoT and these must be addressed before the IoT can reach its full potential.
1. Cybersecurity
One of the biggest concerns is cybersecurity. A vast number of devices are connected to the internet and it is essential to ensure they are secure from cyberattacks. Inadequate security measures is the main factor in hindering the further development snd expansion of IoT.
It is not surprising that security holds such a significance, as failure to ensure adequate data security may lead to costly and disastrous consequences.
2. Privacy
Data protection is of utmost importance. In addition to vigorous tools for authentication, information must be encrypted to safeguard it.
2 Best Practices for Secure Remote Management of IoT Devices
The fact that IoT device management can be undertaken from any remote location is one of the strongest advantages it has. However, many companies have not considered nor established ways to secure remote management. This is even more vital when it involves traversing through public networks.
Below are three of the best practices to ensure secure remote access IoT in any scenario.
1. Apply Security Policies
Ensure security policies for IoT devices are in place thereby creating a framework for how security is deployed and managed e.g. authorised personnel, authorised channels and at authorised times. Additionally, these policies should include privacy protection as well as risk and threat management.
2. Establish Management Procedures
Establish procedures for how devices should be managed such as incident handling and vulnerability management. Additionally, certain procedures need to be established to effectively train users and managers of IoT devices on security.
3. Technical Practices
Device
Ensure that you can securely configure the device remotely, enabling both software and firmware updates over the internet.
Network
Ensure proper identification authentication and authorisation protocols are in place.
Ensure secure communications channels between devices.
Ensure gateways and firewalls are erected to enhance network security.
Data
Ensure that all data is secure, regardless of where it originates or ends up.
4. IoT Remote Troubleshooting
IoT remote troubleshooting refers to identifying and resolving issues with Internet of Things (IoT) devices from a remote location without needing physical access. Some IoT troubleshooting tools include remote desktop tools, network management tools, remote device management tools, and MDM solutions.
Network Management Software
A number of network management software can be used to monitor and manage network devices remotely, including IoT devices, and can help identify and resolve network-related issues. Tools like SolarWinds and Nagios are good examples of network management tools.
Remote Device Management Platforms
IoT-specific remote device management platforms, such as Microsoft Azure IoT Central and AWS IoT provide centralized management and monitoring of IoT devices.
Mobile Device Management (MDM) software
Various MDM solutions can help manage and troubleshoot IoT devices with mobile components, such as smartphones or tablets. The AirDroid Business MDM solution is one of the best examples of MDM solutions.
3 Can You Remote Manage IoT behind Firewall?
Firewall is a security system that manages incoming and outgoing network traffic based on predetermined security rules. Some common uses of firewalls are network security, traffic filtering, and threat protection.
Firewalls prevent unauthorized access to a network and its resources. They can control which types of traffic are allowed to enter or leave the network. They can also protect against various security threats, such as viruses and malware.
Methods to remotely manage IoT behind Firewall
Method 1. Port forwarding Method
This method involves opening a specific port on the firewall to allow incoming connections from the remote management system. The port number and protocol must be specified in the firewall rules.
Method 2. VPN
A VPN server is set up on the network with the IoT devices, and the remote management system connects to the VPN server to access the devices.
Limitations
Complex configuration and security threats are the major limitations to remotely managing IoT devices behind a firewall.
4 AirDroid Business MDM - Secure Configure the Android Device Remotely
With the ever-growing network of devices that are connected to the internet, it may become difficult for businesses to effectively monitor and efficiently resolve issues that may arise. If that’s the case, and you require an IoT solution, then look no further than AirDroid Business MDM.
Key Features of AirDroid Business MDM
Device remote access and control - remotely lock, factory reboot, uninstall apps, access camera, and Black Screen Mode (see below).
Device monitor - view device screen in real-time, device and network status, data usage, location.
Policy Configuration and Android Kiosk mode.
Android app management.
File management.
Secure Remote Access IoT device via AirDroid Business MDM
Remote Control - remote access and control to unattended Android devices without complex settings beforehand.
Black Screen Mode - display of the device can be darkened thereby preventing information from being visible when device is under a remote control session.
Remote Camera - remote connect to the device camera and monitor the device surroundings.
Remote Reboot - reboot the device remotely without sending someone onsite.
Restricted Access - devices may require a higher level of privacy protection. In this case, you can turn on “Restricted Access” on these devices. With this activated, every remote connection will have to acquire device end consent before starting a session.
Voice Call - connect and start a real-time voice call with your device.
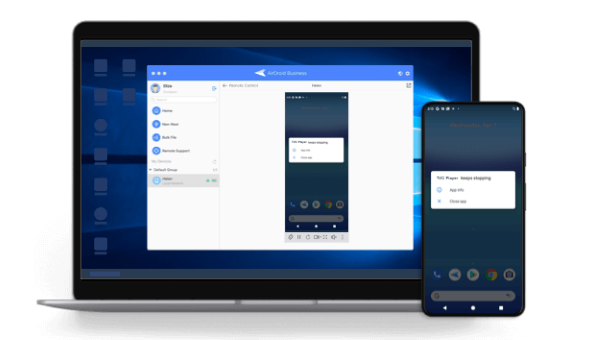
Application Scenarios
AirDroid Business MDM is designed to effectively automate workflow. When using AirDroid Business MDM, you will receive alerts whenever your system finds any abnormalities and will, without human interference, initiate an automated workflow to resolve that issue immediately.
As a direct result of using AirDroid Business MDM, you will noticeably recognise enhanced efficiency and reduced maintenance costs.
There are many types of alert functions and notifications including device offline, data usage, and more. This product can be used by digital signage service providers, Managed IT service providers, and logistic and transportation businesses.
Working principles
AirDroid Business MDM has revolutionised how individuals and businesses operate by allowing them to handle anything from deploying, managing, monitoring and supporting distributed fully managed Android devices.
AirDroid Business MDM offers all-day monitoring to ensure that data access is only available to authorised personnel. This can greatly improve the security of corporate information.
AirDroid has been recognised as one of the best MDM solutions out in the market today by G2, one of the largest and most trusted software marketplaces across the globe. They are dedicated to providing users with the most innovative B2B software solutions, engineered to help businesses grow.
5 Security and Privacy Features of AirDroid Business MDM
Remote management and Monitor
Security and privacy features make it possible to:
Uninstall apps - You can check and uninstall apps from the app list on your device.
Factory reset remotely - When you do this all data will be erased and restoration is not possible.
Put the lock on the device - Once the device is locked, it can only be unlocked with a password.
Alerts
You can monitor metrics on your device by creating alerts. Depending on the activity that you put an alert on, any irregular behavior will result in an alert and let you know that something is wrong. AirDroid Business MDM has around 15 types of alerts.
The list includes battery level, device motion, Sim card removal, Kiosk status, app status, and many more.
Workflow
Once the alert goes on, you can use the option in the workflow to fix an issue without having the device on hand. Remote Troubleshooting options for AirDroid Business MDM include factory reset, remote turn-off of the device screen, reboot, switching to config files, Group transfers, and notification control.
Track & locate
You can get the location of your device anytime with GPS tracking. In addition to real-time location tracking, you can trace the locations of where the device has been. One of the most interesting security features is that you can put a virtual fence around the device.
This way, once it goes out of a specific, market geographical location, you get an alert. You can do the auto-execute actions in this case. For example, once the phone leaves the location, the device locks, or factory reset happens.
Black screen
The black screen mode is one of the AirDroid Business MDM security features that can be handled remotely. The admin has the power to make the device screen dark and turn on the black Screen Mode. When this happens, on the device, the “This device is under maintenance” message will appear.
6 How Remote Access Impacts IoT Devices?
IoT has enabled the individual, small businesses, as well as large businesses of all industries, to work remotely and offsite. It is in an organisations best interest to constantly look for new innovative methods to incorporate IoT to their advantage.
1. Remote Access and Control of IoT Devices
One of the most captivating traits to IoT, is the ability to securely access and control a large number of remote devices from any location in the world (so long there is Internet access).
2. Cost-effective Operation
IoT remote control devices effectively reduce and mitigate expenses by improving productivity and reducing human labour. It allows more efficient utilisation of resources and assets. Employees are able to monitor device performance and conduct (if necessary) adjustments without the need to be physically present.
3. Real-time Monitoring
Predictive analytics and maintenance through real-time monitoring reduces the costs surrounding repairs as problems will be addressed earlier. Prevention is the best solution.
7 Samples of Remote IoT Management for Any Industry
1. Digital Signages
The main advantage of IoT management for digital signage is that it makes it possible to create custom content and access IoT device remotely. It constructs the possibility to improve operational efficiency.
This is archived by allowing the users to make the custom designs remotely which then will be displayed in various locations. Additionally, it is providing information in timely manner, which affects customer experience positively.

Speaking of customers, another huge advantage of IoT management for Digital Signage is that it supports a higher level of customer engagement and therefore, enhances satisfaction. The potential buyer who is around the retail locations gets the latest product news directly.
All this and “customized greetings” works like a trigger and as a result, more customers make decisions to enter the store.
2. Manufacturing
IoT is having a significant impact on the manufacturing industry. Manufacturers can collect important operational data with use of IoT devices. This data can be invaluable as it helps them improve efficiency and reduce costs.

Additionally, manufacturers are using IoT devices to connect with customers and suppliers, allowing for more effective and efficient sharing data such as orders and shipments, thereby improving the coordination between the suppliers and customers.
3. Transportation and Logistics
The transportation industry is currently undergoing a metamorphosis as the IoT becomes more advanced as well as being more prevalent. For example, a smart car can receive real-time updates on traffic conditions and navigation instructions. This will make travel much safer and less congested, reduce emissions, and save both time and money.

Additionally, vehicle-mounted computers (called ELDs) allow businesses to monitor delivery drivers and their cargo during transportation. Remote IoT has begun to revolutionise this sector amongst others.
4. Warehousing
Implementation of remote IoT systems can be utilised for accurate inventory management, tracking of supply volumes as well as monitoring environmental conditions such as internal temperature, humidity etc.

8 FAQs about Remote Access to IoT Devices
9 Learn More: What is the Best Way to Secure IoT Devices?
As mentioned, there are risks and vulnerabilities associated with securing IoT Devices, and in order for IoT to achieve its full potential, security policies and procedures must be implemented to safeguard enterprise infrastructure, and reduce the risk of systems from being compromised.
Below are some recommendations gathered from multiple sources, including the Broadband Internet Technical Advisory Group (BITAG) and the Cloud Security Alliance.
Secure access logs of IoT devices and train security teams to recognise DDoS attacks.
Use encrypted protocols to secure communications.
Create more effective and secure password policies and utilise sign-on tools to manage and limit access.
Implement restrictive network communications policies, and set up virtual LANs.
Ensure secure firmware update policies for the device.
Improve failover design.



Leave a Reply.