What can MDM Monitor? How does MDM Monitoring Work?
Monitoring is one of the reasons that enterprises become users of Mobile Device Management software. There are several benefits:
- Detect any abnormal user behavior and take immediate actions remotely.
- Inspect poor working devices at once and maintain them remotely.
- Better control access and usage of devices to improve work efficiency.
- Check location to prevent device loss.
True, benefits go far beyond these. In this article, we will go deep into the monitoring system, including available monitored items and how to use it.
Part 1 : What is MDM and its Monitoring System?
Mobile Device Management is a necessary initiative if companies have their own work-used devices or that adopt bring-your-own-device (BYOD) and company-owned personal enable (COPE) device policy. By means of MDM software or EMM/UEM providers, organizations are allowed to manage all devices in a central system.

Monitoring system is an important part of the management mechanism in order to protect company resources. After enrolling in an MDM console, a device is under the admin's observation.
MDM monitoring system usually works together with other features for device security, for example:
- Remote control - lock, wipe, or troubleshoot devices remotely
- Policy - setup rules to allow or disallow system settings
- Alerts & workflow - preset triggers and implement automated actions
- Geofencing - track location in real-time
With the mentioned features, the admin can easily apply remote monitoring management to endpoints whether mobile devices or dedicated devices.

Part 2 : Is it Legal to Have MDM Monitoring Employee's Device?
Privacy issues are frequently related to MDM monitoring, in particular when the organization uses MDM on personal phone for work.
It's worth knowing that a Mobile Device Management tool does have the capability to get equipment-related data like OS details and app details by accessing the device. But, it does not mean that the organization has unlimited power to view the device user's secret.
To get data or use monitoring features require permission from device owners in advance. Without the user's approval, the MDM software is not allowed to collect information.
Furthermore, it's unable to gain permission secretly. Because the MDM software must comply with app developer policies.
Take Android and Apple for instance.
As Android developer policy center states, "....must be transparent in how you handle user data. ...the access, collection, use, handling, and sharing of user data from your app, and limiting the use of the data to the policy compliant purposes disclosed. " (Read more about Privacy, Deception and Device Abuse)
Apple also illustrates how apps can access private data, "must request permission to access: Personal data, including location, health, financial, contact, and other personally identifying information; Device capabilities like camera and microphone..." (Read more about Accessing private data)
Part 3 : What can MDM Solutions Monitor?
In short, the mobile device management solution can see and can't see the following items.
What MDM can see:
Phone model; OS version; device info such as battery and RAM; app name and version; device location; etc.
What MDM can't see:
Personal text; email; files (including photos); browser history; app account and content; contacts; financial and payment information; authentication information; etc.
More specifically, the MDM monitoring system is mainly used for checking device status, network status and usage, traffic-consuming conditions on apps, user logs, and preset policies working status.
Then, how does the monitoring system work on the mentioned aspects?
1Device
In the Monitor dashboard, you can see the online status, network status, battery capacity, MDM software version, and others.
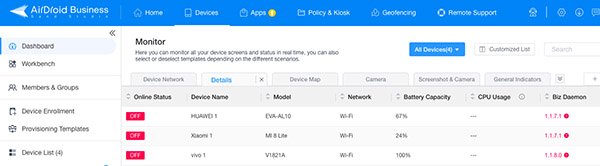
Network monitoring is available to check how many devices are using WiFi and Cellular, signal quality, and daily data usage.
Besides, the MDM tool is also available to track device location but requires online devices. As for screen monitoring, it will need permission to access camera and is often used in unattended devices.
Other details that an MDM can monitor on devices: available storage, battery temperature, permission condition, external HDMI/SD card status, etc.
With the provided info, companies can find if there's an unusual circumstance then remote control and troubleshoot the equipment.
2App
After enrolling the device to the MDM console, the app info shows as follows:
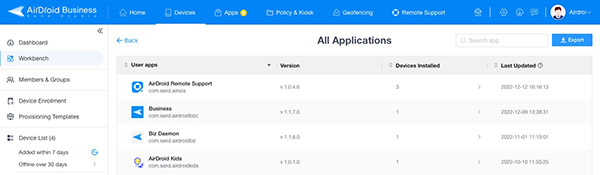
MDM solutions can view the installed app names, versions, and last update time. They can monitor the traffic usage of each app as well.
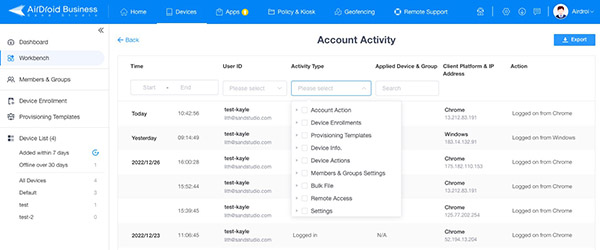
3User
The Mobile Device Management tool will monitor user activity if he is invited.
4Others
If a device is applied with Kiosk Mode or has used Policy, the status can be viewed in Monitor dashboard. This can prevent the device from exiting the setting accidentally.
Part 4 : How to Use MDM Monitoring?
Using an MDM monitoring system involves different steps for different actions. You need to follow it up for a smooth running of your requirements. So,
1. Add Devices to MDM Console
When you add up the device to the automated monitoring system MDM, you need to grant Biz Daemon (software for devices being controlled by AirDroid MDM) some special permissions so that you can monitor and remote control the device.
These accessibilities need to activate: file and media; microphone; camera; location; and so on.
Device user can change permission easily by visiting Biz Daemon anytime after deployment.
2. View Device Details in the Dashboard
Go to the dashboard and check the info. Here you can monitor the device status, network, location, and screen.
3. View Data Usage, App Info and User Activity in Report
Go to the Devices bar, select workbench, and move to the reports bar. You can choose one to check related details.
Part 5 : How to Manage Employee Devices with MDM and Avoid Offending?
Companies can manage employee devices while still respecting their privacy. With clear communication and careful configuration, companies can ensure data security while minimizing any potential offenses caused by MDM monitoring.
1. Assign company-owned work-used mobile devices to employees so the company can fully control the device and how they're used. This is a great way to ensure that confidential company data and sensitive information are safe and secure.
2. For personal devices that use in the workplace, use Mobile Device Management (MDM) software that only has access to the employee's work account. This can help balance the need for data security with privacy concerns.
3. Make sure to communicate to employees what information the company may access and why. This will help ensure that employees are aware of their privacy rights and minimize any potential offense caused by the implementation of MDM. A guideline is necessary before connecting devices to the organization.
4. If the admin has to remote control a device, for example, to delete data, he should inform the user in advance and explain.





Leave a Reply.