How can I set up password rules with Android Password Policy in AirDroid Business?
We have created a YouTube video to help you understand this guide better and faster.
.
Video Tutorial: How can I Set up Password Rules with Android Password Policy in AirDroid Business
AirDroid Business's MDM Password Policy Settings feature provides the flexibility to either ask the end-user to set a password aligning with company standards or to set a device password yourself. Additionally, you can establish rules to reset the Android device in case of a security breach attempt.
This tutorial will guide you through the process of setting, enforcing, and managing password policies on your devices.
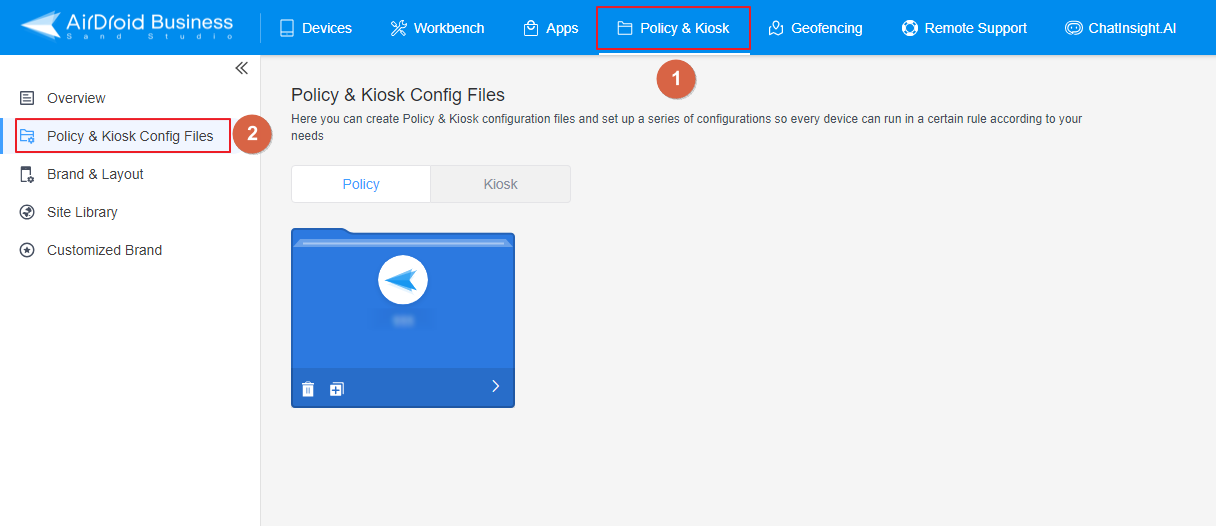
- Step 1Access Policy Setting
- Log into Admin Console and switch to the 'Policy & Kiosk' section. From there, navigate to 'Policy & Kiosk Config Files'.
- Step 2Establish or Edit a Policy
- In this section, you have the option to either create a password policy or modify an existing one.
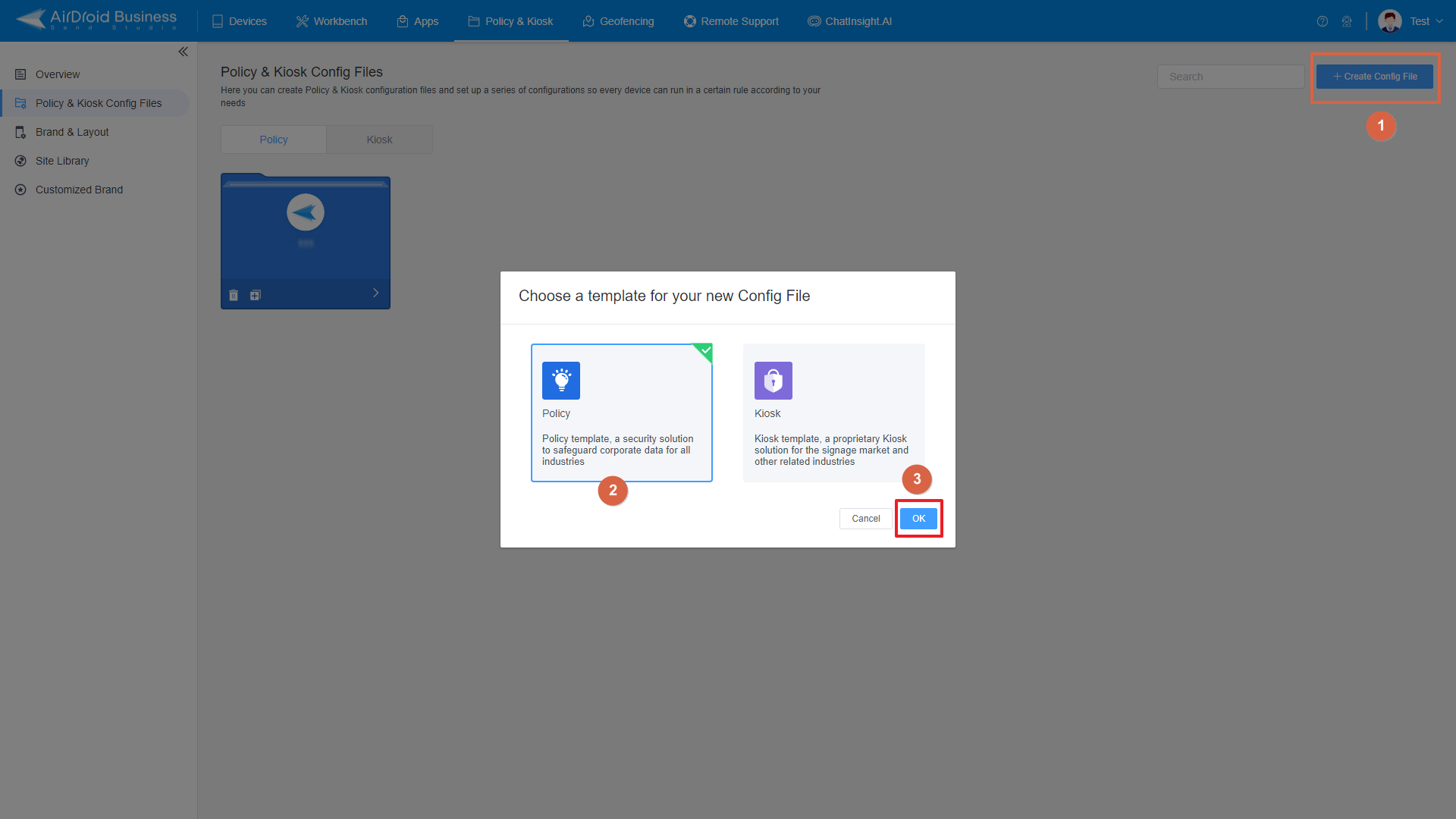
- To create a new policy, click on "+Create Config File", choose "Policy" and then click "OK" on the pop-up.
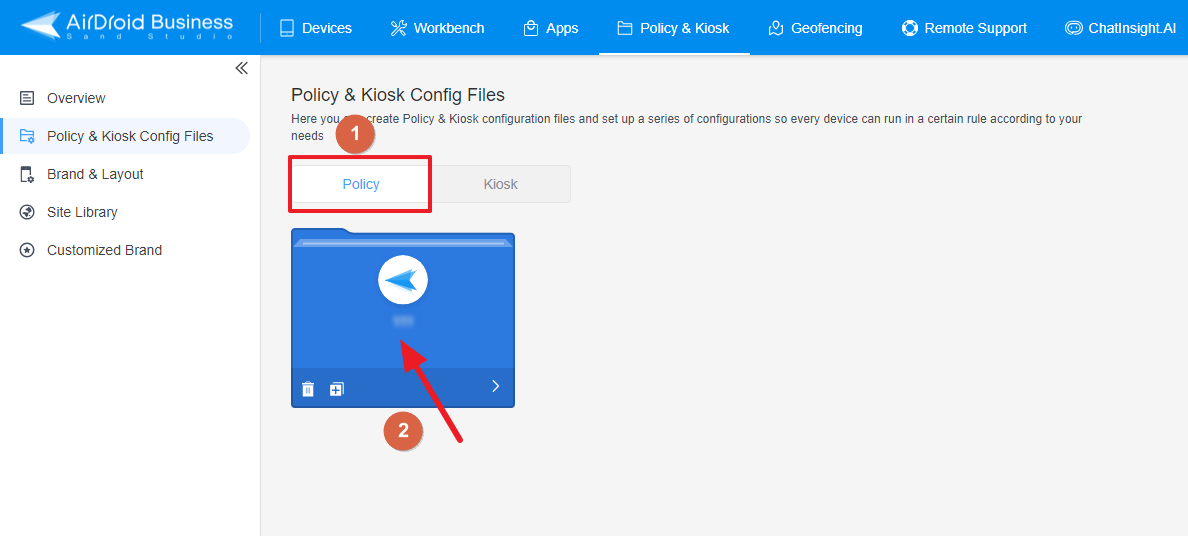
- To modify an existing Policy, switch to the "Policy" tab, and select the Policy File you want to modify, and click on the "Edit" Button in the top right corner. On the following page, you can set all kinds of limitations and settings for your config file.
- Step 3Go to Password Settings
- Locate the 'Password' section. This is where you'll create or edit your password policies.
- Step 4Configure Password Policy Settings
- Here, you'll be able to implement a password policy configuration. You can create a password based on your preferences and establish the rules for the screenlock password. You have three main options:
- After selecting this configuration, you can set password complexity rules for the screenlock. Users can unlock the device by entering a password that complies with the these rules.
- The rules include:
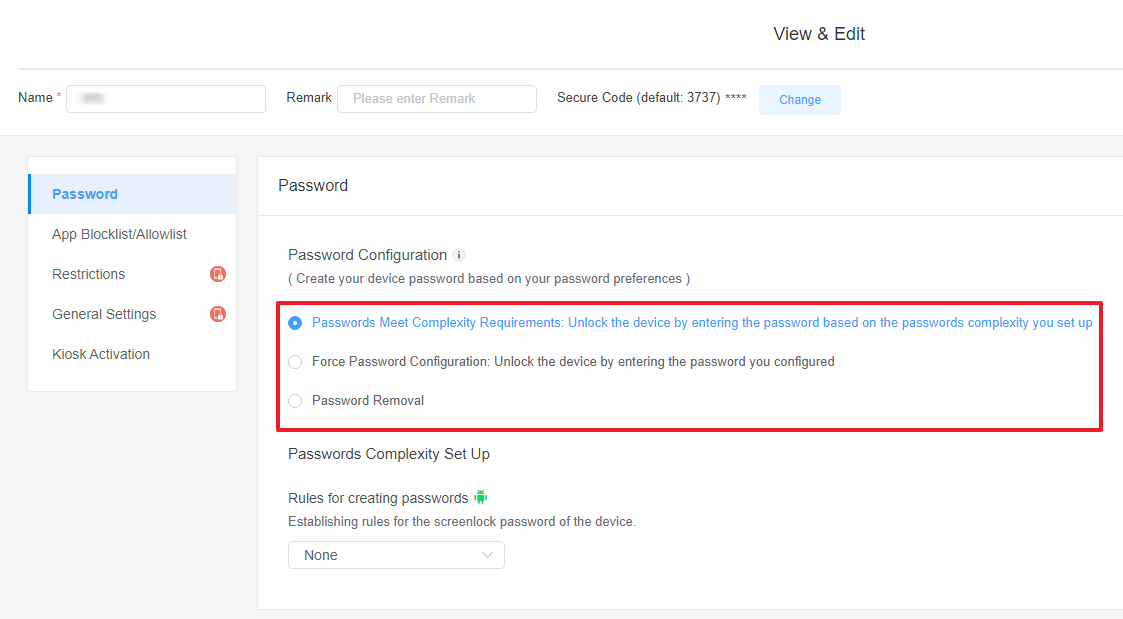
1Passwords Meet Complexity Requirements
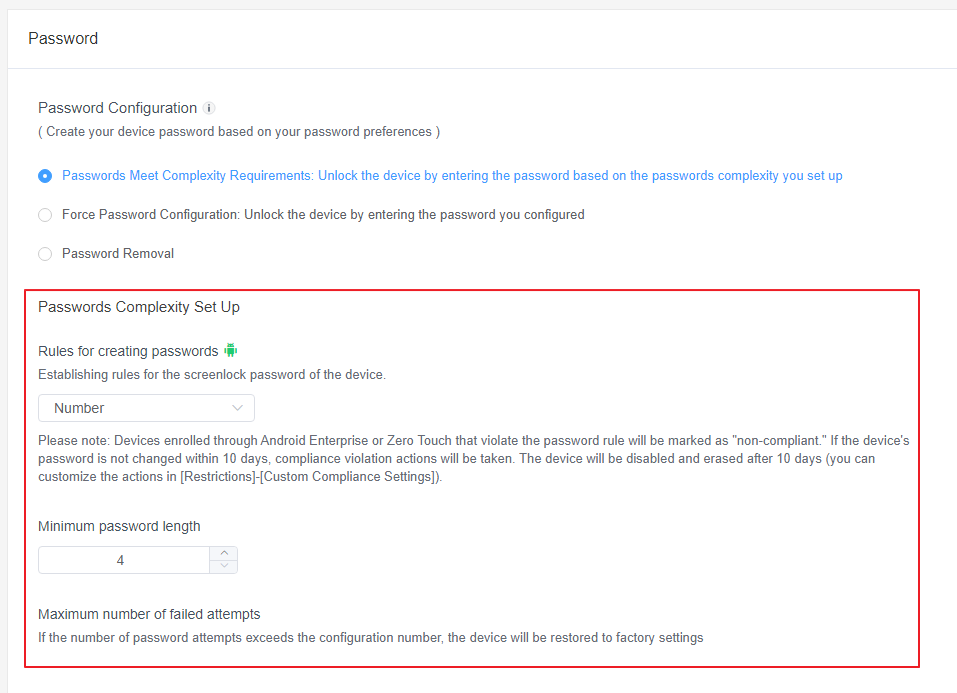
- Character Rules:
You can set the rules password policy for the type of password characters. By clicking the drop-down box to select, you can set the password to be composed of numbers, alphabets, or a mixture of numbers and alphabets.Note : Devices enrolled through Android Enterprise or Zero Touch that violate the password rule will be marked as "non-compliant." If the device's password is not changed within 10 days, compliance violation actions will be taken. The device will be disabled and erased after 10 days (you can customize the actions in [Restrictions]-[Custom Compliance Settings]).
If you want to know more about Custom Compliance Settings. Please refer to this article.Note : Certain devices with Android 7.0, 7.1.1 and 7.1.2 may not take effect after the configuration due to the system issue. - Minimum Password Length:
Set up the minimum length requirements for your passwords, ranging from 4 to 16 characters. - Maximum Number of Failed Attempts:
Set a limit for incorrect password attempts before the device resets to its factory settings. This number can range from 4 to 16. - Password Valid Period:
You can set a valid period for your passwords by clicking the drop-down box. You need to reset them after the expiration. - Configure Password Reuse:
Set the number of passwords a user must change before they are allowed to reuse a previously used password. There are four options:
None; Don‘t allow reused passwords; Prevent reusing the last 5 passwords; Prevent reusing the last 10 passwords; Prevent reusing the last 20 passwords - Smart Lock:
Users can bypass the password prompt on the device lock screen by configuring trust agents such as On-Body Detection, Trusted Device, etc.
In most instances, setting an eight-character password is the best password length security policy because it can provide adequate security and make users easily remember.
2. These settings only take effect when AirDroid Biz Daemon has the Device Owner permission on the device.
3. Support devices with Android 5.0 and above.
4. Devices enrolled through Android Enterprise or Zero Touch are not supported.
After these rules were set up, users can unlock the device by entering a password as requires by the security policy.
2Force Password Configuration
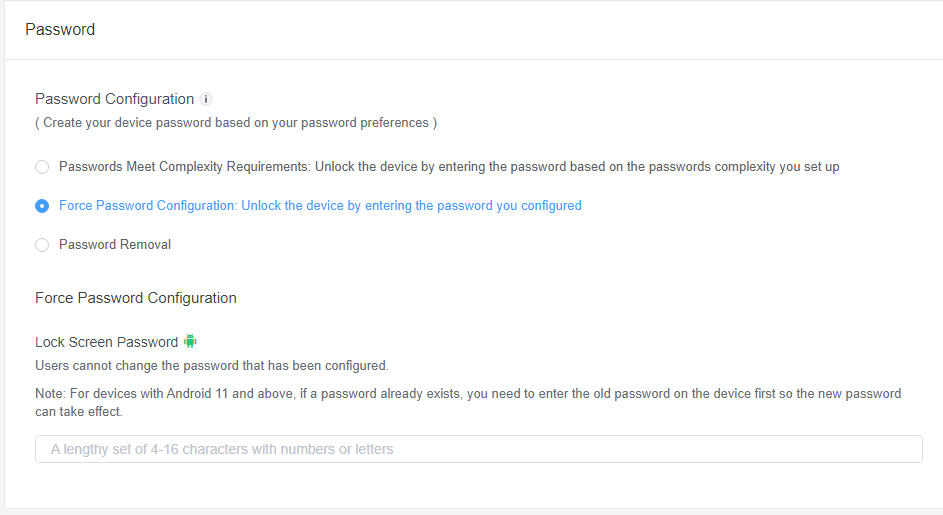
By selecting this option, you can configure a specific password. Users can only unlock the device by entering the password you configured.
This ensures users cannot change the password that has been configured.
You can set a lock screen password with a length of 4-16 characters with numbers or letters.
Devices with Android Enterprise Enrollment are not supported.
For devices with Android 11 and above, if a password already exists, you need to enter the old password on the device first so the new password can take effect.
3Password Removal
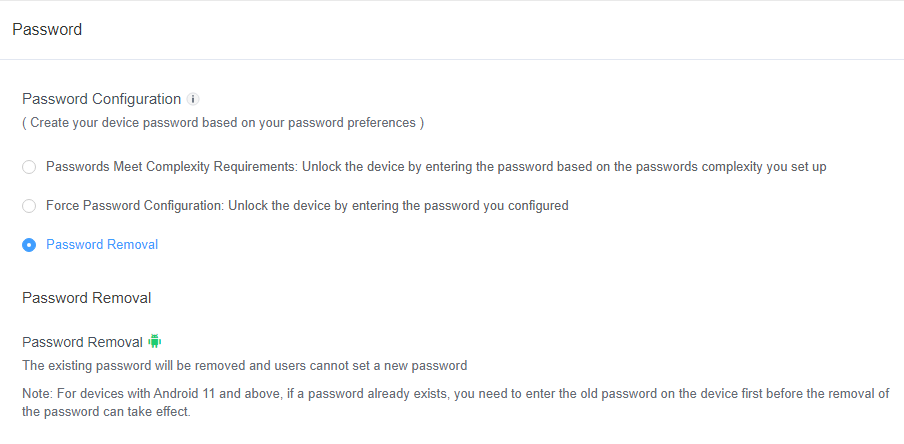
If you wish to remove an existing password, you can choose this option.
Existing passwords will be removed, and users will be unable to set new ones.
For devices with Android 11 and above, if a password already exists, you need to enter the old password on the device first so the new password can take effect.
2. 1. For devices with Android 11 and above, if a password already exists, you need to enter the old password on the device first before the removal of the password can take effect.
- Step 5Save and Implement the Policy
- After setting up your password policy, click 'Save' button.
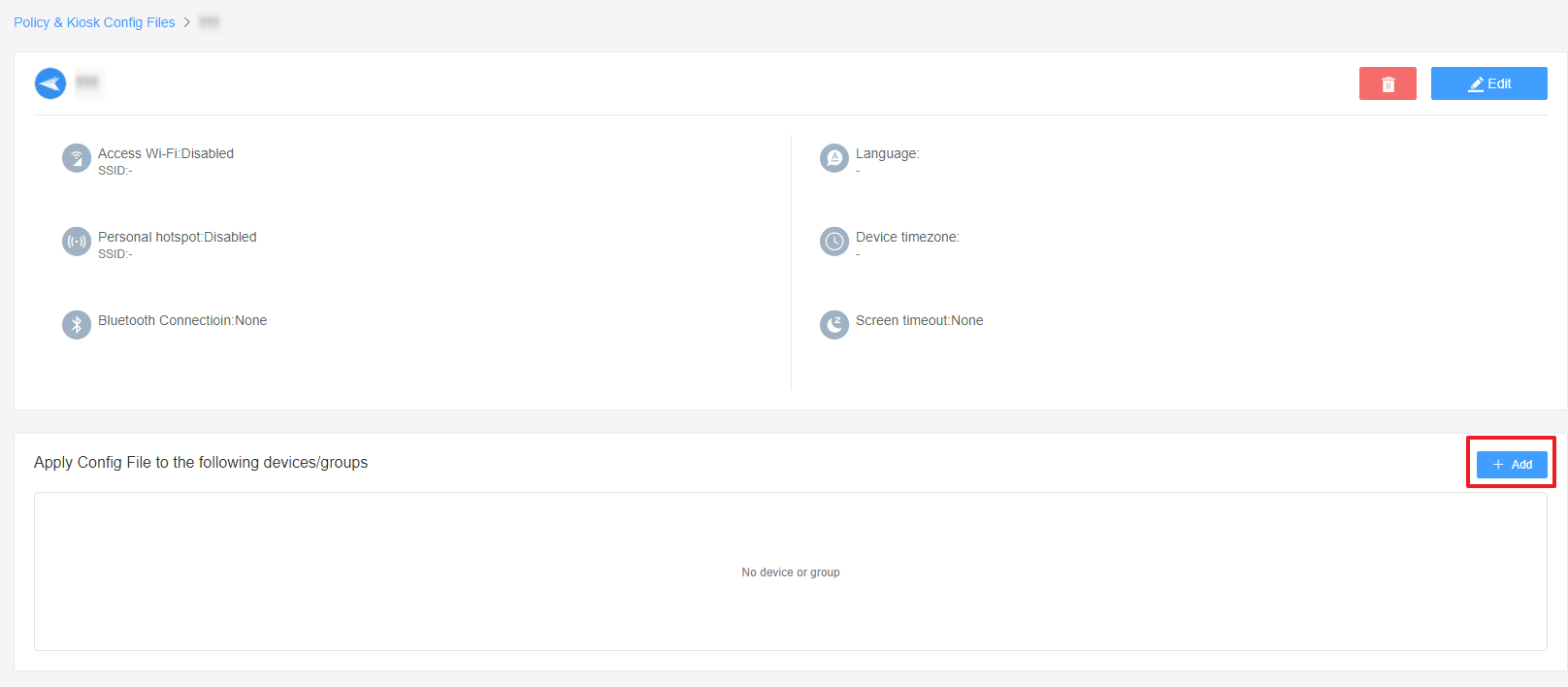
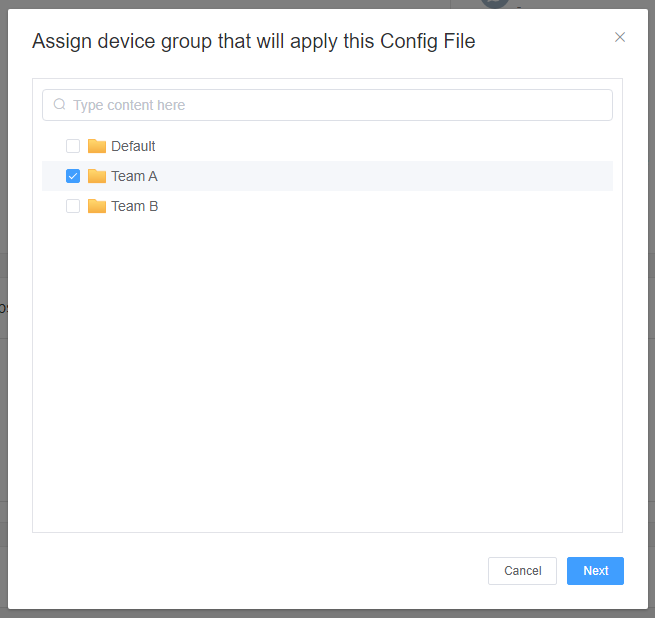
- Return to the 'Policy Files Management' section, select the policy you just created or edited, find the [Apply Config File to the following devices/groups] and click '+Add'. Choose the devices or groups you want to apply the policy to and confirm.
Congratulations! You've successfully set up password policies for your devices with AirDroid Business. Regularly updating these policies will help ensure the security of your organization's devices.
Still need help? Submit a request >>
Related Articles
- How to implement App Blocklist/ App Allowlist on AirDroid Business?
- How can I control camera access using Camera and Lockscreen Camera Settings in AirDroid Business?
- How do I manage Microphone Permissions in AirDroid Business?
- How can I ensure data security with Mandatory Storage Encryption in AirDroid Business?
- How can I set up System Update Policy in AirDroid Business for optimal performance?
You May Also Like
- How to use App Allowlist for Kiosk Mode in AirDroid Business?
- How to Set up Kiosk Website Allowlist on AirDroid Business?
- How to set up Kiosk Browser Settings on AirDroid Business?
- How do I Customize the Kiosk Brand within AirDroid Business?
- How to Modify My Brand and Layout in Kiosk Mode of AirDroid Business?

