[Must-Know] How to Check If Someone Is Remotely Accessing Your Computer
Remote access is a convenient way to access another computer remotely. However, did you know that Americans lost $806 million in 2022 due to remote access scams (tech support scams)? Moreover, remote access scams are up by 52% in Australia during Q1 2024.
Remote access scams are terrifying. A third party secretly watches all your computer activities, accesses your accounts and data, and even pushes you out of your computer. So, if you are curious to know how to check if someone is remotely accessing your computer, then stick around.
In this guide, we will list signs to detect if someone is remotely accessing your computer and then list some effective measures to block unautomated remote access.

Part 1. Things to Know Before Checking
1Can Others Access My Computer Remotely Without Me Knowing?
Yes, other people can access your computer remotely without you knowing. There are now many tools and techniques that can help hackers access your computer remotely. For example, remote access software, like TeamViewer, AnyDesk, and similar others, can give hackers complete control of your computer and even the ability to have unattended access.
Imagine that you received a fake support call. The person created a sense of urgency that your computer was vulnerable and should be fixed. You were convinced to install the remote access software and give access to your computer to troubleshoot the issue. That's it! Now, the hackers have complete access to your computer.
Other than the above approach, hackers can also access your computer through other means, like software vulnerabilities, malware, etc.
2Can You Tell When Someone Looks at Your Computer Remotely?
Yes, if you keep a close eye on your computer activities, you can suspect if someone is looking at or accessing your computer remotely. If you suspect unexpected cursor movement, new software installed, increased CPU usage, unusual network activity, and similar things, it can tell that someone is looking into your computer remotely.
Yes, if you keep a close eye on your computer activities, you can suspect if someone is looking at or accessing your computer remotely. If you suspect unexpected cursor movement, new software installed, increased CPU usage, unusual network activity, and similar things, it can tell that someone is looking into your computer remotely.
Part 2. How to Check if Someone Is Remotely Accessing Your Computer
There are many ways to detect if hackers are accessing your computer. Below, we have shortlisted five ways on how to tell if someone is accessing your computer remotely:
1Look for Intrusion Signs
If your computer is being accessed remotely, there will definitely be some signs of intrusion. Your job is to suspect those signs and then take action accordingly.
Here are some commons signs about how to know if someone is remotely accessing your computer:
- Unexpected Cursor Movement: You may notice the mouse cursor moving on its own without your input.
- Unfamiliar Software Installed: You may notice unfamiliar software installed on your computer.
- Sudden Pop-ups or Error Messages: You may get sudden pop-ups, error messages, or Command Prompt windows popping and closing immediately.
- Alerts from Antivirus Software: Your antivirus software is sending you alerts on suspicious activities.
- Higher Network Activity: Your data consumption has increased significantly than usual.
- Active Camera or Microphone: Your camera or microphone may be active without your permission.
- Unknown Activities on Your Accounts: You may notice unauthorized logins, changes in personal information, new user accounts, and other unknown activities on your online accounts.
All the above signs are the indication that your computer may be under remote access by hackers.
2Check Your Computer's Recent Activities
Hackers won't just sit and watch you; they will try to perform different activities on your computer. So, another way for how to check if someone is remotely accessing your computer is to look into your computer's recent activities:
- Check Recently Accessed Apps/Files:
For Windows, go to the Start menu and look at the recently accessed apps/files.
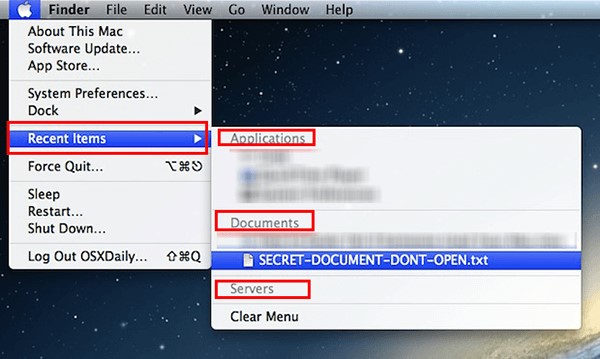
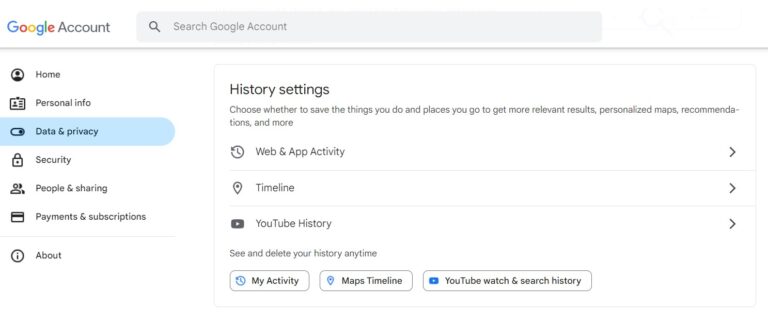
For macOS, click the Apple icon and then tap Recent Items to see recently accessed apps/files. - Check Browser History: Check the browser history to see if you find unknown websites, downloads, or extensions. You can also go to the "My Activity" setting in Chrome to thoroughly see the browser history.
- Check Login Events: Check your login events to see failed login attempts or unusual computer access during strange day/night hours.
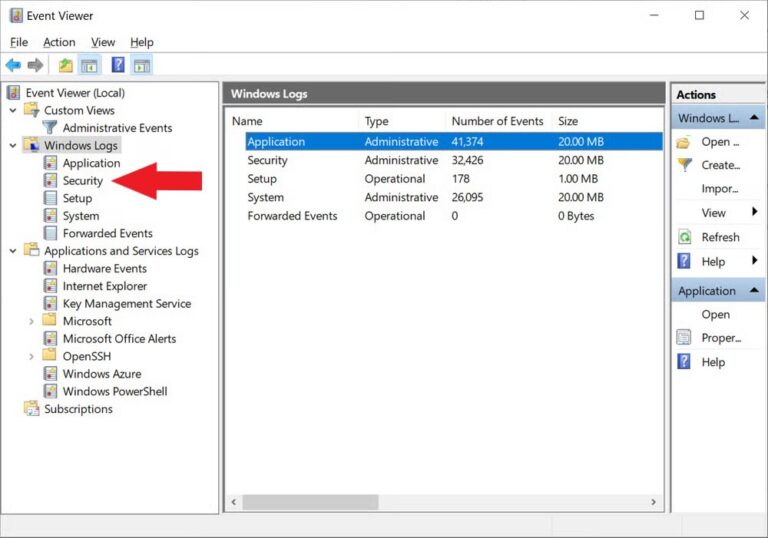
For Windows, navigate to Control Panel > System and Security > Administrative Tool > Event Viewer. Select "Security" from the left side and review all login events.
For macOS, use reliable third-party software to record and review login events.
3Interrogate Remote Access Programs
To access your computer remotely, the most common tactic is to install a remote access program in your computer and then use it to access your computer.
Check the Presence of Remote Access Program:
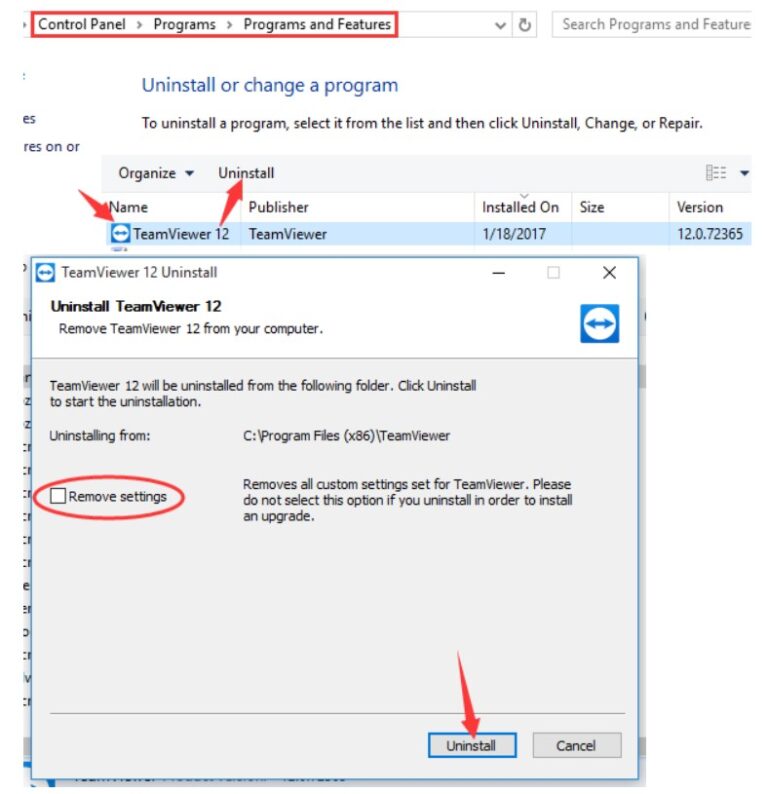
If you haven't installed any remote access program, then you should check the list of currently installed programs. Check if any remote access program is present on your computer, like AnyDesk, TeamViewer, etc. If yes, immediately uninstall it.
Check Remote Access Program Activities:
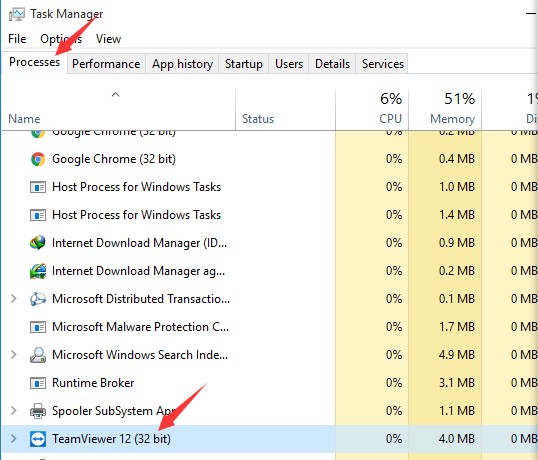
If you use a remote access program for personal or work-related activities, you should check it under the currently running programs list. If you are not currently using the tool, it shouldn't be running on your computer. If it is still active, it indicates that scammers are using it in the background.
To check remote access program activities, launch Task Manager (for Windows) or Activity Monitor (for macOS) and view the running status of the remote access program.
4Check Your CPU Usage
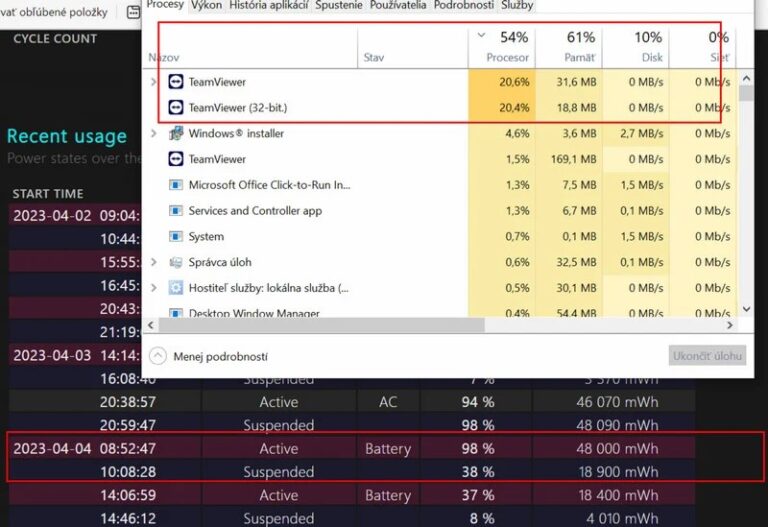
CPU usage is another excellent way on how to know if someone is remotely accessing your computer. A high CPU usage when you are not running any power-hungry programs is an indication that some unknown processes are running in the background.
You can access CPU usage status from the Task Manager (for Windows) or Activity Monitor (for macOS). However, high CPU usage does not always mean unauthorized remote access. Sometimes, a program may be getting updated in the background, which can also lead to high CPU usage.
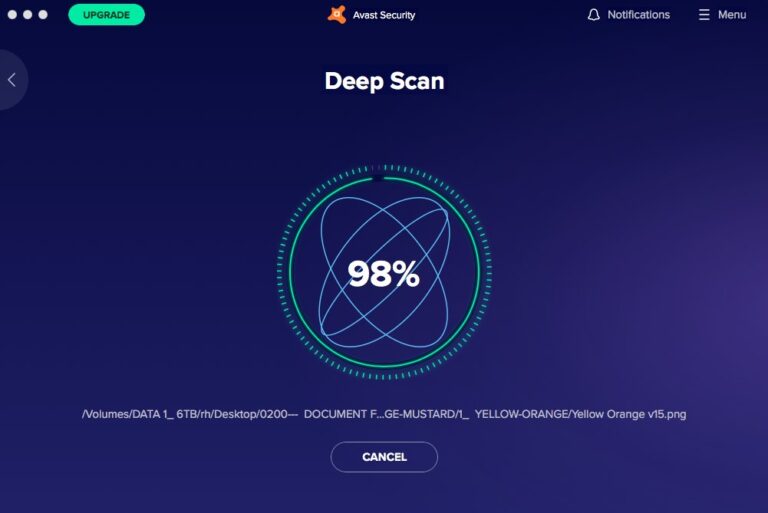
5Perform a Deep Antivirus Scan
The last way on how to tell if someone is accessing your computer remotely is to perform a deep antivirus scan. An antivirus tool can deeply scan all your computer programs and files. If it finds any malicious software or files, it will notify you and remove them. This will also be an indication that your computer is compromised.
Part 3. How to Block Unauthorized Remote Connections
If you are sure that someone has made it into your computer and is now accessing your computer remotely, don't waste any more minutes. Quickly follow the below steps to block unauthorized remote connections right away:
1Disconnect from the Internet Immediately
The Internet is the main source through which a scammer can access your computer. Once you disconnect the internet, you break the connection between your computer and the scammer. This now gives you time to diagnose your computer, remove malware or malicious software, and secure your accounts.
2Change Passwords from Another Secure Computer
If the scammer has been accessing your computer remotely for a while, they may also have your accounts' passwords. So, the next step is to change passwords.
To do so, use another secure device, such as a computer or a smartphone, and change the passwords of all your accounts, including banking, social media, email, etc. Try to create strong and different passwords from your previous ones.
3Scan and Remove Malicious Programs Using Antivirus Software
Now that your accounts are secured, your next move should be to detect and remove malicious programs from your computer.
First, manually check the list of your installed programs from the Control Panel (on Windows) or the Applications folder (on Mac). If you find any unknown or suspicious software, uninstall it. Secondly, also remove any remote access software you have installed.
Next, install antivirus software and let it scan and remove all the malicious programs and files.
4Backup Data and Factory Reset Your Computer
To ensure that your computer becomes free from any traces of hidden malware, you should factory reset your computer. However, make sure you backup your computer data first on a cloud or external hard drive.
5Secure Your Network Connection (Router)
Today's malware is capable of penetrating other devices linked with your Wi-Fi router. Therefore, the last step is to secure your network connection as follows:
- Change the router login credentials.
- Enable WPA3 or WPA2 encryption.
- Disable the remote administration settings.
- Update the firmware of the router.
That's it! This way, you can block unauthorized remote access and remove all the traces of malware or malicious tools in your computer.
Conclusion
With digital advancements, remote access scams are growing and becoming more sophisticated. Above, we have listed the potential signs of how to check if someone is remotely accessing your computer and then what mitigation steps to take. So, keep a close eye on your computer and avoid getting into the traps of remote access scams.
Furthermore, when you need remote access for work-related activities, make sure you choose secure remote work software like AirDroid Remote Support.






Leave a Reply.